Automated Partitioning of Android Applications for Trusted Execution Environments
When software systems are put on different platforms, new issues start to dominate their quality argument. In particular, for mobile systems the security and trustworthiness of an application and device are paramount. At the same time, much of software security concerns cannot be completely relieved with thorough software testing and design, whereas in the context of mobile applications, even the operating system (OS) cannot be trusted to provide security guarantees.
My work in this area tackles the issue of adaptation and reuse of existing mobile applications to take advantage of the hardware backed protection. This work views security as a combined responsibility of software and hardware.
Abstract:
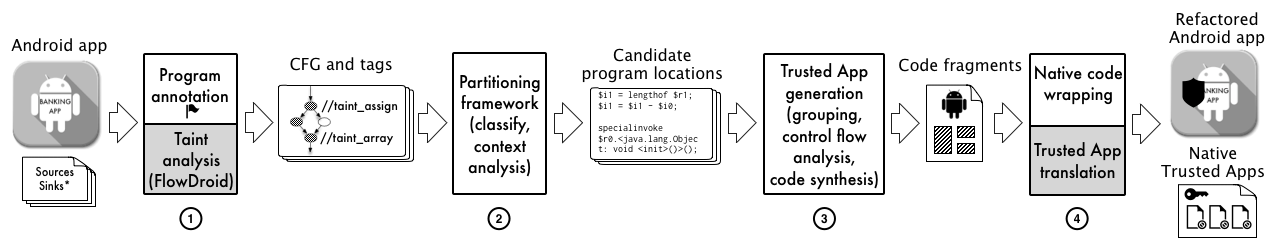
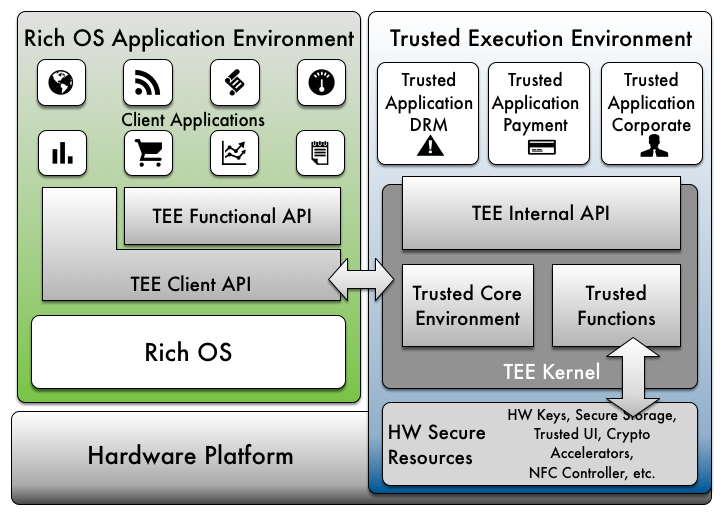
The co-existence of critical and non-critical applications on computing devices, such as mobile phones, is becoming commonplace. The sensitive segments of a critical application should be executed in isolation on Trusted Execution Environments (TEE) so that the associated code and data can be protected from malicious applications. TEE is supported by different technologies and platforms, such as ARM Trustzone, that allow logical separation of “secure” and “normal” worlds. We develop an approach for automated partitioning of critical Android applications into “client” code to be run in the “normal” world and “TEE commands” encapsulating the handling of confidential data to be run in the “secure” world. We also reduce the overhead due to transitions between the two worlds by choosing appropriate granularity for the TEE commands. The advantage of our proposed solution is evidenced by efficient partitioning of real-world applications.
Bibtex record
@inproceedings{Icse2016Partition,
Author = {Rubinov, Konstantin and Rosculete, Lucia and Mitra, Tulika and Roychoudhury, Abhik},
Title = {Automated Partitioning of Android Applications for Trusted Execution Environments},
Booktitle = {Proc. of 38th Int. Conf. on Software Engineering (ICSE)},
Doi = {10.1145/2884781.2884817},
Isbn = {978-1-4503-3900-1},
Numpages = {12},
Pages = {923--934},
Series = {ICSE '16},
Year = {2016},
Url = {http://doi.acm.org/10.1145/2884781.2884817}}
Published and presented at the 2016 IEEE/ACM 38th IEEE International Conference on Software Engineering